In this blog post, we look at security from a software development and applications perspective. We explain why software security is important, look at security best practices, and how your development team can write secure software applications.
By the time you’ve read this article, you should have a good understanding of how you can ensure that your software applications are secure!
Why should you be aware of software security best practices?
Hackers, malicious users or even disgruntled employees can cost businesses a lot of money. Whether it be by installing a virus onto a network, finding loopholes in existing software, or simply by copying unauthorized data from a network.
Protect your brand, reputation, customers, and products
Hackers and cybercriminals are always coming up with ways to compromise networks and software applications. Sometimes these breaches can have a massive effect on the reputation of your brand or online services that you offer.
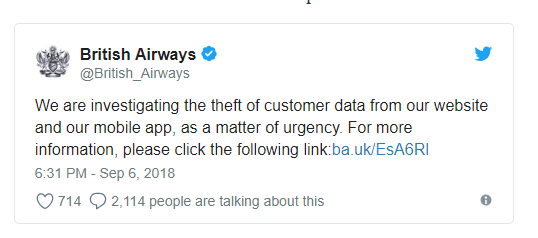
In the UK, for example, British Airways experienced a hacking incident this year where almost 400,000 sets of payment and customer details were stolen!
The firm could only apologize and had to launch an urgent investigation. Customers who made bookings through the airline’s app were advised to contact their bank and credit card providers. Incidents like this have a massive effect on the brand, perception and potential new customers will think twice about sharing their payment details with the online booking service. It pays to be aware of software security!
Universities Hacked
In March of this year, the Department of Justice indicted nine Iranian hackers over a spree of attacks on more than 300 universities in the United States and abroad! The DoJ went onto report that 31 terabytes of data were stolen, worth an estimated $3 billion is intellectual property! The attacks used spear phishing emails to trick professors and other university associates into clicking on malicious links and entering their network login credentials.
Security best practices
With some examples of high profile hacking cases, here are some steps you can take to ensure that the software you use is running on a secure platform and network.
System Patches
A lot of attacks exploit known vulnerabilities associated with old or end of life software applications. Take time to ensure that any software you run is stable and has the recommended patches installed. This is one of the most effective security measures you can deploy to help mitigate any security risks.
Automation
Hackers often resort to automation when trying to compromise software applications or operating systems. For example, they may write scripts to brute force password guessing attempts or repeatedly attack firewalls. Deploy automation yourself to automate daily security checks and processes to free up your security teams time to focus on more strategic initiatives.
Enforce Least Privilege
Users need permission to go about their daily activities but not all users are equal! For example, if you’re running SQL Servers, don’t assign application users with administrator access unless it’s necessary.
Network Segmentation and Isolation
Isolating your network into segments is an important practice as it can restrict the movement of data or the servers that a hacker can move between. For example, your application production data or environments should be on a different network or subnet from your development and test environments.
Monitor activity
So, you’ve got automation in place, log files are being created and you’re enforcing least privilege where appropriate. You still need to monitor daily activity in some capacity – perform periodic monitoring activities to key systems and networks, and look out for suspicious activities such as privilege abuse or user impersonation.
Measure
Perform an audit of key metrics that are important to your business, for example, the number of web requests or database hits per hour. Use this information in conjunction with other security practices to help you assess normal business activity from potential hacks taking place!

Writing secure software applications
So, we’ve looked at why you should be concerned about software security and some security best practices. Now we turn our attention to some points in terms of writing secure software from a developer’s perspective.
With most data breaches being executed against data services in the cloud, security in software development is equally important. Fortunately, there are some tried and tested techniques and best practices that developers can deploy to ensure that the software they develop is robust, secure and helps protect data and users.
OWASP, the Open Web Application Security Project, with headquarters in Maryland, is a community that provides resources to help business and development teams around the world ship secure software. The community has compiled in-depth recommendations which you can read more about here in detail. That said, here are the top 10 web application security risks the initiative has identified and what developers can do to prevent these from happening:
1. Injection
Injection flaws, such as SQL injection, LDAP injection, and CRLF injection, occur when an attacker sends untrusted data to an interpreter that is executed as a command without proper authorization.
* Application security testing can easily detect injection flaws. Developers should use parameterized queries when coding to prevent injection flaws.
2. Broken Authentication and Session Management
Incorrectly configured user and session authentication could allow attackers to compromise passwords, keys, or session tokens, or take control of users’ accounts to assume their identities.
* Multi-factor authentication, such as FIDO or dedicated apps, reduces the risk of compromised accounts.
3. Sensitive Data Exposure
Applications and APIs that don’t properly protect sensitive data such as financial data, usernames, and passwords, or health information, and could enable attackers to access such information to commit fraud or steal identities.
* Encryption of data at rest and in transit can help you comply with data protection regulations.
4. XML External Entity
Poorly configured XML processors evaluate external entity references within XML documents. Attackers can use external entities for attacks including remote code execution, and to disclose internal files and SMB file shares.
* Static application security testing (SAST) can discover this issue by inspecting dependencies and configuration.
5. Broken Access Control
Improperly configured or missing restrictions on authenticated users allow them to access unauthorized functionality or data, such as accessing other users’ accounts, viewing sensitive documents, and modifying data and access rights.
* Penetration testing is essential for detecting non-functional access controls; other testing methods only detect where access controls are missing.
6. Security Misconfiguration
This risk refers to improper implementation of controls intended to keep application data safe, such as misconfiguration of security headers, error messages containing sensitive information (information leakage), and not patching or upgrading systems, frameworks, and components.
* Dynamic application security testing (DAST) can detect misconfigurations, such as leaky APIs.
7. Cross-Site Scripting
Cross-site scripting (XSS) flaws give attackers the capability to inject client-side scripts into the application, for example, to redirect users to malicious websites.
* Developer training complements security testing to help programmers prevent cross-site scripting with coding best practices, such as encoding data and input validation.
[bctt tweet=”How can your development team write secure software applications?” username=”GAPapps”]
8. Insecure deserialization
Insecure deserialization flaws can enable an attacker to execute code in the application remotely, tamper or delete serialized (written to disk) objects, conduct injection attacks, and elevate privileges.
* Application security tools can detect deserialization flaws but penetration testing is frequently needed to validate the problem.
9. Using Components With Known Vulnerabilities
Developers frequently don’t know which open source and third-party components are in their applications, making it difficult to update components when new vulnerabilities are discovered. Attackers can exploit an insecure component to take over the server or steal sensitive data.
* Software composition analysis conducted at the same time as static analysis can identify insecure versions of components.
10. Insufficient Logging and Monitoring
The time to detect a breach is frequently measured in weeks or months. Insufficient logging and ineffective integration with security incident response systems allow attackers to pivot to other systems and maintain persistent threats.
* Think like an attacker and use pen testing to find out if you have sufficient monitoring; examine your logs after pen testing.
Summary
In this article, we’ve looked at software and application security, the OWASP Top 10 security vulnerabilities, and how development teams can help thwart attacks.
Here at Growth Acceleration Partners, we have extensive expertise in many verticals. Our nearshore business model can keep costs down whilst maintaining the same level of quality and professionalism you’d experience from a domestic team.
Our Centers of Engineering Excellence in Latin America focus on combining business acumen with development expertise to help your business. We can provide your organization with resources in the following areas:
- Software development for cloud and mobile applications
- Data analytics and data science
- Information systems
- Machine learning and artificial intelligence
- Predictive modeling
- QA and QA Automation
If you’d like to find out more, then visit our website here. Or if you’d prefer, why not arrange a call with us?