What’s your vendor assessment process for security checks like?
If it still means sending out 200+ question surveys every time you bring on a tech/SaaS partner, you already know how draining that can be.
The answers often come back vague, exaggerated, and sometimes too generic.
As a tech lead, you shouldn’t have to spend weeks chasing paperwork just to feel confident your vendor can protect your data. Even worse, that process can’t assure security and privacy in this AI era.
But there’s a better way to validate your vendors.
In this article, we’ll walk you through the industry-recognized security practices you can look for in your vendors, including SOC 2. These are the standards that give you proof so that you can move quickly with confidence instead of second-guessing.
How AI Makes Security and Compliance Non-Negotiable
Organizations have never taken data security and privacy lightly. A recent CISO report confirms that security and risk management remain the top 5 priorities for leaders year after year.
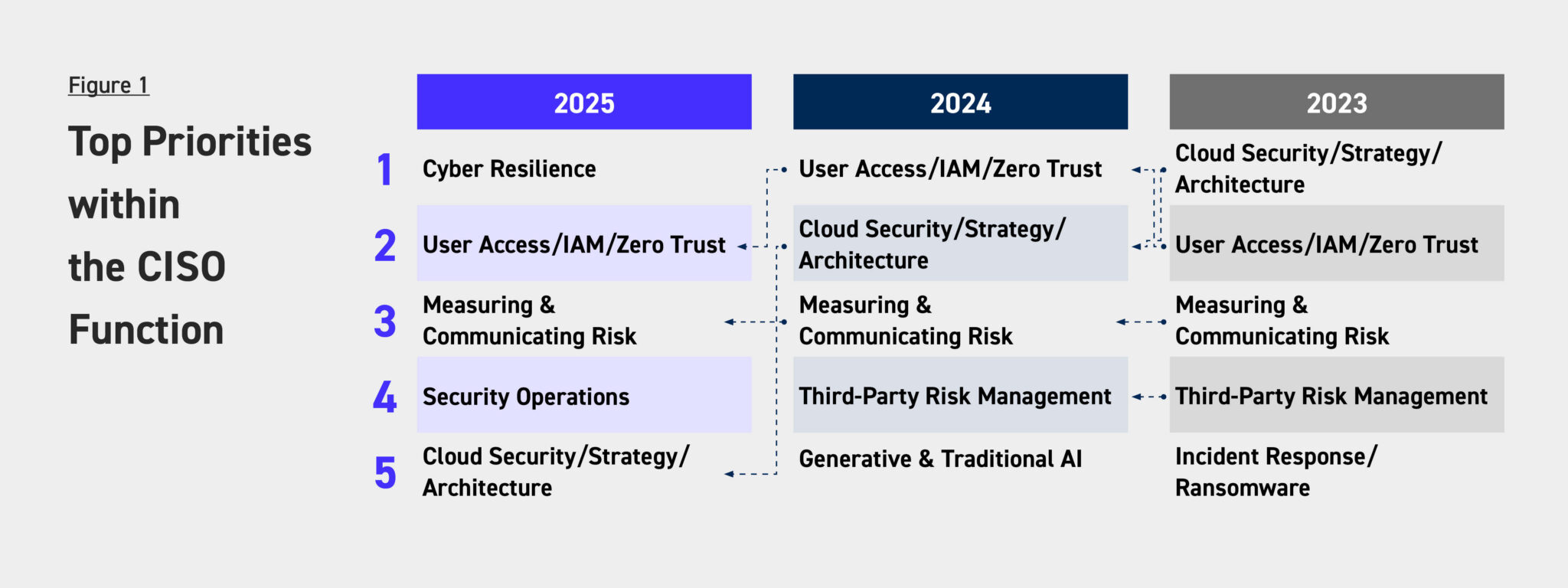
Source: Evanta – CISO Report
Surprisingly, AI has not climbed as high on that list, and for good reason. Leaders know security has to be stronger than ever. The same technology that helps businesses automate defenses is also available to cybercriminals, who use it to scale and sharpen their attacks. AI has become an amplifier, fueling both innovation and risk.
The data from McKinsey and Global Security Outlook 2025 tells the story about AI amplifying security concerns better:
- McKinsey reports a 1200% surge in phishing attacks since generative AI went mainstream in 2022.
- 72% of organizations have seen an increase in cyber risks, with ransomware still top of mind.
- 47% worry about AI-powered attacks, yet only 37% have a process to assess the security of AI tools before deploying them.
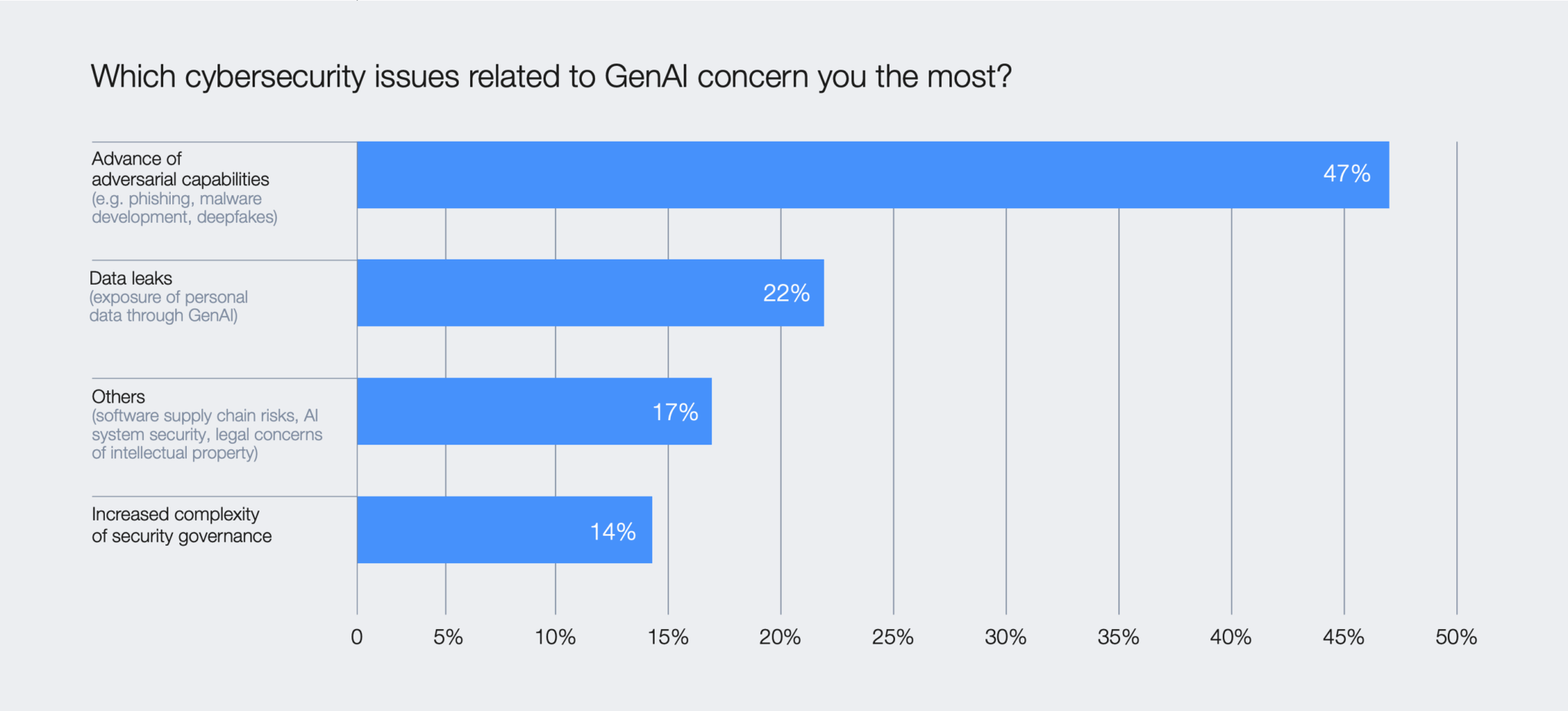
The adoption of AI and other emerging technologies is creating vulnerabilities that a manual approach to security checks and defenses can never keep up with. That’s why your manual and routine security questionnaires are below the standard.
Handing over your data without verifying a vendor’s security practices is like giving someone the keys to your house without knowing if they’ll lock the door behind them. It leaves your business open to data leaks, poisoned AI models, regulatory fines, and reputational damage.
As Rob Greig, CIO at Arup, put it after a major cyber incident,
“Cybersecurity alone is not enough. Building resilience requires a culture of critical assessment and the ability to spot red flags across an organization.”
Security is a core business investment, and should be treated as one.
Vendor assessments may feel complex, but industry-standard practices now make it easier and far more reliable to validate a partner’s security posture. We’ll look at them shortly.
Industry Standards That Set the Bar for Security Validation
With so many moving parts across different industries and organizations, it can feel like there’s no perfect way to evaluate whether a partner will protect your data. That’s why industry bodies stepped in to create processes that bring order, consistency, and assurance to the process.
Organizations like the American Institute of Certified Public Accountants (AICPA) developed standards to give businesses a reliable way to assess vendor data security practices. This framework, along with others, serves as proof of trust and an independent validation that a company is following recognized best practices.
As a tech/IT leader, this shifts the guesswork and endless questionnaires to evidence-backed assurance. Instead of relying only on what a vendor claims, you can look for industry-approved reports and practices that speak louder than words.
Here are some of the most recognized standards that set the bar for vendor security validation:
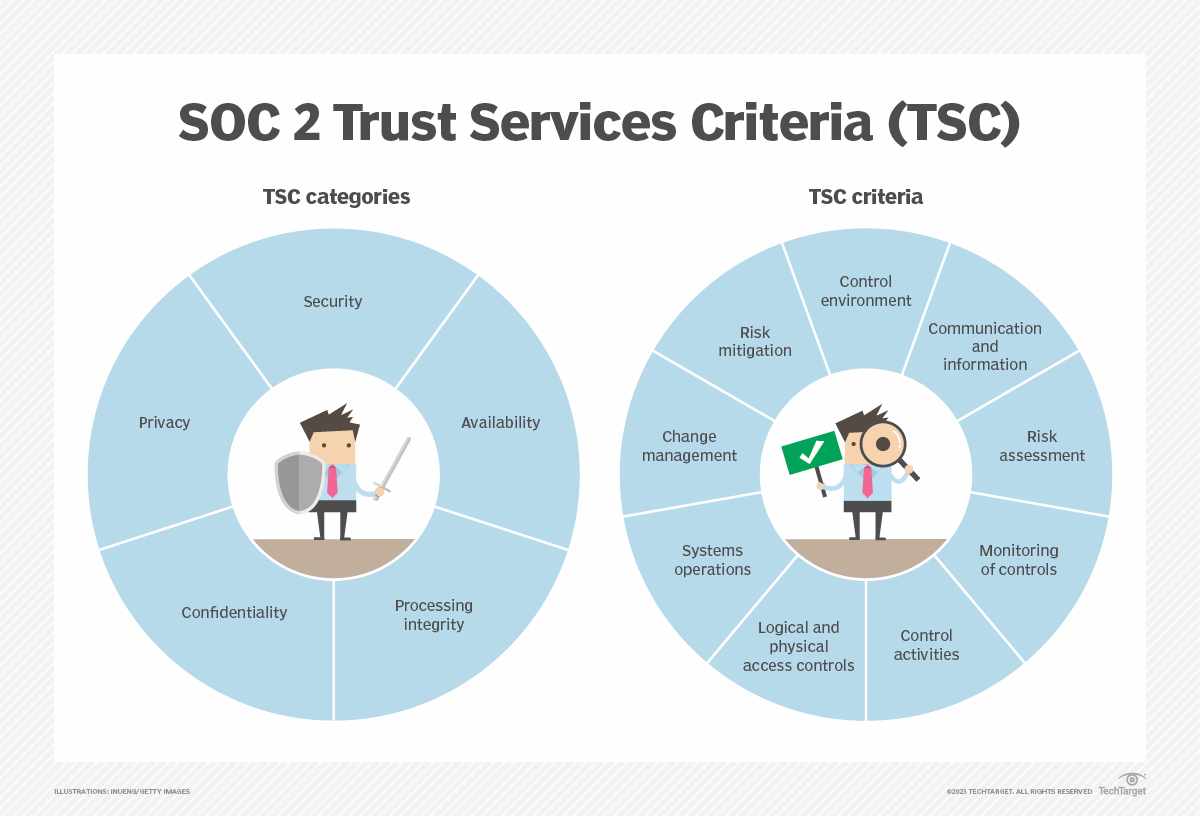
SOC 2
SOC 2, System and Organization Controls for Service Organizations, is an auditing framework created by AICPA. Its purpose is mainly to provide organizations with a reliable way to evaluate how a vendor manages and protects customer data.
The framework is built around five trust service principles: security, availability, processing integrity, confidentiality, and privacy.
During a SOC 2 audit, independent auditors review a firm’s systems and processes against these principles to verify whether they meet the required standards.
Source: TechTarget
Then they document their findings as a report to share with businesses that need the firm’s service. This makes it easier to choose vendors with confidence and cut down the uncertainty in risk assessments.
GDPR (General Data Protection Regulation)
This regulation is one of the world’s most recognized data privacy regulations, applying to any organization handling the personal data of EU residents. This means organizations outside the EU region that have customers, employees, or a branch in this region need to prove their data privacy compliance.
GDPR emphasizes user consent, transparency, and accountability in how organizations collect and process data. For clients, GDPR compliance is a clear sign that a vendor respects privacy rights and meets strict international standards for safeguarding personal information.
This also assures that whatever product the vendor develops for you follows the required standard, saving you from paying future fines.
Other Recognized Standards
Beyond SOC 2 and GDPR, there are several other well-established practices and frameworks that underscore how seriously organizations treat data security and privacy:
- HIPAA (Health Insurance Portability and Accountability Act): This pertains to the data privacy and security of health information in the U.S. healthcare industry. As a business in the health tech industry, you should review a tech vendor for this data management practice.
- PCI DSS (the Payment Card Industry Data Security Standard): This is specifically for the payment industry. The goal is to secure credit and debit card information to help businesses protect customers from fraud and financial breaches.
- CCPA (California Consumer Privacy Act): This is a California law that gives consumers greater control over their personal information. It’s a country-specific data protection regulation that shows the growing importance of privacy rights across the U.S.
Our Security Milestone at GAP: SOC 2 Audit
Security is a non-negotiable part of doing business today. That’s why we underwent an independent SOC 2 Type I audit, a rigorous process that tested every internal control, reviewed every procedure, and validated that our security practices are more than policies on paper.
The result is the SOC 2 report that you can rely on. Instead of chasing long questionnaires, you can request the report directly from the auditors and gain assurance that we manage your data with the highest level of care and oversight.
The audit confirmed that our security practices are consistent across all our processes from:
- How we identify and reduce risks before they reach our clients
- How we train employees to apply secure practices every day
- How we evaluate and manage the vendors and partners we work with
For us, this certification is an achievement, but for you, it’s proof that:
- Your data is protected by tested and validated controls
- We’re prepared to reduce risk and meet compliance requirements
- You can move forward with confidence, knowing security is never an afterthought
- Vendor onboarding is faster, with fewer questionnaires and delays
- You can adopt AI-driven solutions and new technologies without second-guessing data protection
Conclusion
When you’re choosing a tech partner next time, simplify your security validation procedures. Instead of asking whether you can trust a vendor with your data, look at the industry-recognized standards they’ve achieved.
SOC 2 audit review is one of those standards, and it’s evidence you can rely on. For us at GAP, this SOC 2 independent audit milestone reflects our ongoing commitment to keep raising the bar on security and protect your data.
Request our SOC 2 report today, and let’s talk about how we can support your next project with confidence.